Windows Azure, as an application host platform, must provide privacy, integrity and user’s data availability. It must also provide transparent reliability to allow users and their agents to manage through their own and Microsoft tracking services.
This document describes a large number of controllers implemented in Windows Azure. Users can decide whether these capabilities and controllers are suitable for their unique needs. This overview starts with the technical test of security functions from the perspective of users and Microsoft business, including the extended identity and access management driven by Windows Live ID, the usage of bidirectional SSL authentication, the isolation of layered environment and components, the state maintenance and configuration integrity of virtual machines, and the triple redundant storage which is provided to minimize the impact of hardware failure. Other than the discussion of the technology, it also mentions how to monitor, record and report the reliability of the technical support of Windows Azure in the users’ cloud environment.
Right after the discussion of technology, this document also mentions the personnel and process to help make Windows Azure more safe, It includes SDL principle, control operator and management mechanism, and physical security features, such as user’s choice of region, data device, access and power redundancy, which are recognized by the world in the development process.
This document ends with a brief discussion of the specification. Norms have a continuous influence in IT enterprises. Although the responsibility for complying with laws, regulations and industry requirements lies with the users of Windows Azure. Microsoft’s commitment to providing infrastructure security facilities and the expanding range of tools to meet the special challenges of users are extremely important to Microsoft’s own success. And these are also the key to the success of our users using Windows Azure Platform.
Introduction
1.Foundation of Security Models
Users’ Perspective: Computing, Storage, Service Management
Windows Azure Perspective: Fabric
Cloud Security Design
Privacy
Identity and Access Management
Quarantine
Encryption
Data deletion
Integrity
Usability
Development Cycle Security
Service Operation
Microsoft Operator
Security Response
Network Management
Remote management of Fabric Controllers
4. Physical Security
Device Access
Redundancy and Fail-over
Medium
User Alternative Geographic Location
Control
ISO 27001 Certification
Further reading of references
Glossary
Windows Azure(microsoft practice examscheck that) is a cloud service operating system, including development, service hosting and service management on Windows Azure Platform. Windows Azure provides developers with on-demand computing and storage through Microsoft Data Center, which enable them to lodge, expand and manage web applications on the Internet. By using Windows Azure, Microsoft lodges at data and programs belonging to users. Because of that, Windows Azure must solve the information security challenges which is beyond the traditional IT solutions. This document describes the controllers that users of Windows Azure can use to achieve the security level that they need, and determines whether these capabilities and controllers can adapt to their unique needs.
Readers and Scope
The target readers of this white paper include: developers who are interested in creating applications running on Windows Azure, technical decision makers who are considering the usage of Windows Azure to support new or existing services.
The focus of this white paper is on the Windows Azure Operating System as an online service platform component, without any detailed description of Windows Azure Platform components, such as Microsoft SQL Azure, AppFabric, or Microsoft Code name “Dallas”. The discussion focuses on the security features and functionality of Windows Azure.
Although this article provides a minimum of general introduction information, readers still need to be familiar with the basic concepts of Windows Azure (and refer to other references provided by Microsoft). At the end of the document, you can find links to more other references for further reading.
The final part of this document also contains a glossary, which is underlined in bold in this document.
Foundation of safety mode
Before having a research on the deeper Windows Azure Security Feature Technology, this part provides a simple overview of its security mode. After that, the overview assumes that readers are familiar with the basic concepts of windows Azure, and mainly focuses on security related features.
Users’ Perspective: Computing, Storage, and Service Management
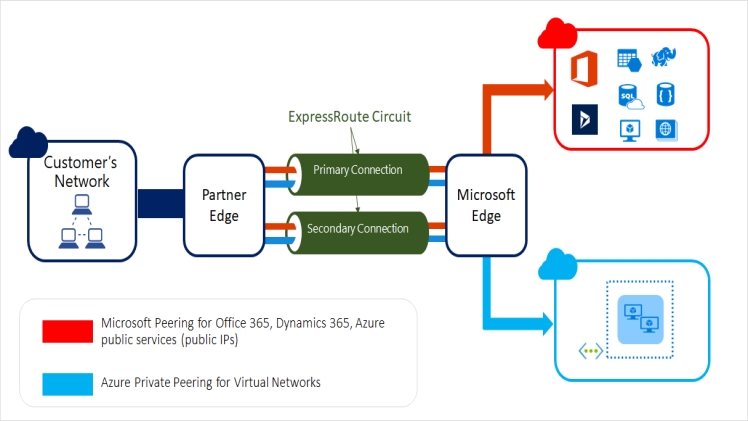
Figure 1: A Brief Overview of the Key Components of Windows Azure
As shown in Figure 1, Windows Azure provides two main functions: cloud-based computing and storage. On the basis of this, users can create and manage applications and associated configurations, and users can manage applications and storage through . A typical subscription can be created by associating a new or existing identity certificate with a credit card on the Subscription Page. The subsequent access to the subscription system can be controlled by a Windows Live ID(https://login.live.com. Windows Live ID is one of the longest running Internet authentication services which still exist. It provides windows Azure with a strictly tested guard system.
A subscription can include no or many storage accounts. A managed service contains one or many deployments. A schedule contains one or many. A character contains one or many instances. The storage account contains binary data blocks, tables, and queues. Windows Azure Driver is a special binary data block type. The access control and storage accounts of managed services are managed by subscription. The function of authenticating a Windows Live ID associated with a subscription provides full control right of all managed services and storage accounts under that subscription.
Users upload the developed applications through Windows Azure Portal or program through Service Management API (SMAPI) to manage their host services and storage accounts . Users can access Windows Azure Portal through browsers or SMAPI through command tools (by programming or Visual Studio),
The authentication of SMAPI is based on the common / private key pairs created by the users and the self signed certificate registered through Windows Azure Portal. This certificate will be used in subsequent SMAPI access. SMAPI will queue the requests in Windows Azure Fabric, and then Windows Azure Fabric takes over the requests, initializes and manages the required applications. Users can monitor and manage their applications through Portal or programmable SMAPI using the same authentication mechanism.
Access to Windows Azure storage is managed by the storage account key. The key is stored on each account. The storage account key can be reset by Windows Azure Portal or SMAPI.
Computing and storage capacities further constitute the basic functional units of Windows Azure. Figure 2 provides a more granular view, exposing these basic units and illustrating their connections to the components described earlier. All the components discussed so far are summarized as follows:
Host services include deployment, roles and.
The storage account includes binary data blocks, tables, queues and.
These definitions are defined in the glossary, and a detailed description of them can be found in the general materials of Windows Azure. Here is a brief introduction to preparation for the deeper discussion on the security features of Windows Azure in the rest of this document.
The main Windows Azure topics, objects, and authentication mechanisms are summarized in Table 1 as follows:
Table 1 Summary of Windows Azure Authorization Mechanism
Figure 2: Granular Description of Window1s Azure Components and Relationships.
Windows Azure Perspective: Fabric
We have elaborated the Windows Azure components that can be managed by users from an upper level perspective. Next, we will further explore the Fabric under the basic computing and storage of Windows Azure. Although we have said that users can control Fabric through defined management interfaces, the main purpose of Windows Azure is still the management of abstract virtual infrastructure. It can simply present consistent and expandable resource sets for the users. In short, the developers don’t need to manage these virtual infrastructures, which are all done by Microsoft. This section will introduce some basic components in Windows Azure Fabric directly managed by Microsoft.
Based on the number of role instances specified by users, Windows Azure provides a virtual machine (VM) for each role instance, and then runs these roles on these virtual machines. These virtual machines run on specially designed platforms (Windows Azure Hypervisor) using Cloud Technology. A virtual machine is a specialized application and it runs on a managed operating system called FAs Management (hosted in the users’ virtual machine). FAs also manages storage nodes. Windows Azure Management Program, Root OS / FA, and users’ VMS / gas are together as one.
FAs is managed and FC exists beyond the computing and storage nodes (computing and storage are managed by independent FCs). If a user updates his applications when the system is running, FC will communicate with FA, FA will then contact GA, and GA will notify the applications to report the configuration changes. In case of hardware failure, FC will automatically find the available hardware and restart the virtual machine on the new hardware.
Fundamentally or basically speaking, just like any other application hosting platforms, Windows Azure must provide privacy, integrity and users’ data availability. It must also provide transparent reliability to allow users and their agents to manage through themselves and Microsoft Tracking Services. After the description of the basic components and their relationships, this section will explain how Windows Azure provides these classic features of information security.
Privacy ensures that users’ data can only be accessed by authorized entities. Windows Azure provides privacy through the following mechanisms:
Identity and Access Control – ensures that only appropriate authenticated entities are allowed to be accessed.
Isolation – minimizes data interaction by ensuring logical and physical separation of appropriate containers.
Encryption – is used inside Windows Azure to protect the controlling channels and provide them to the users who need strict data protection mechanisms.
More details about how to implement these data protection mechanisms in Windows azure are as follows:
Identity and access management
The most robust security control mechanism can not prevent the attackers who obtain unauthorized identity information and key. Therefore, identity information and key management are key components in security design and implementation of Windows Azure.
All the main authentication and authentication mechanisms have been introduced before, and they are summarized in Table 1. This part provides a deeper description, including APIs, Application Priority, Key Distribution and Authentication for trusted subsystems (such as Fabric Controller).
SMAPI Authentication
SMAPI provides Web services through protocol, which is provided to users and developers through Windows Azure Tools. This protocol runs on SSL and uses a certificate and a private key created by the user to authenticate. This certificate does not require a trusted check certificate issuer (CA). You just need a self signed certificate and associate the fingerprint of the certificate with the subscription through Windows Azure Portal. As long as the users have the control over the keys and the Live IDs used to create the accounts, this method would provide a high degree of security, ensuring that only the entities authorized by the users can access specific parts of the service.
Least Privilege of Users’ Software
Running applications with the least privilege is widely regarded as the best practice of information security. In order to keep pace with the principle of least privilege, the users are not granted the administrator rights to the virtual machine. By default, users’ software runs in a low privilege account in Windows Azure (in future versions, users can choose different privilege models according to their needs). This reduces the potential impact and increases every complexity of attack that requires elevated privileges to conduct the attacks in addition to obtaining vulnerabilities. It also protects users’ services from attacks by their own end users.
SSL Mutual Authentication of Internal Control Traffic
The communication of all internal components of Windows Azure is protected by SSL. In most cases, SSL certificates are self signed. The exceptions might be the certificates and FC used in the connection of the external access to Windows Azure Network.
FC has a certificate issued by Microsoft CA, and it has a trusted root CA. FC’s public key can be used by Microsoft Development Tools. In this way, when developers submit new application impressions, they can be encrypted by FC Public Key to protect any internal secret information.
Certificate and Private Key Management
In order to reduce the risk of exposing certificates and private keys to developers and managers, they are installed through a separate mechanism different from that using their codes. The certificate and private key are uploaded in a file format of PKCS12 (PFX) through SMAPI or Windows Azure Portal. The upload process is protected by SSL. These files can be protected by the passwords. But if so, the password must be included in the same message. SMAPI provides a Password Protection Mechanism (if necessary), and uses SMAPI public keys to encrypt the whole PKCS12 data block, stores it at a data storage point on a private FC, and also stores short certificate names and public keys as metadata.
The configuration data associated with the roles in the same subscription specifies the certificate required by the roles. When a role is being initialized on a virtual machine, FC gets the corresponding certificate, decodes the PKCS12 data block, encrypts it with the FA Public Transmission Key, and sends it to FA on the node. FA on the node sends it to GA on virtual machine of initialization role, then GA decodes it and installs it on data storage point of the operating system, and marks that the private key can be used but not exported. After the installation, all temporary certificate copies and keys are destroyed. If you need to reinstall, the certificate must be repackaged by FC.
Hardware Certificate Used by FC
Access Control of Windows Azure Storage
Windows Azure Storage has a simple access control model which has been discussed earlier. Each Windows Azure subscription can be created with one or several storage accounts. Each storage account has a key for controlling access to all data in the storage account. This supports a scenario where associated applications are stored and those applications have full control over their associated data. We can get a more mature access control model by creating user applications in the fore-end of storage, giving the application a storage key, allowing the user program to verify remote users, and even giving the authorization to a single request.
Those two mechanisms support general access control scenarios. Part of the data in the account where the data is stored can be marked as publicly readable, in which case reading the data is available without the shared key signature. This is mainly used to access non-sensitive data, such as web images.
Another mechanism is called Shared Access Signature (SAS). It is a process, knowing the given Storage Account Key (SAK), and being able to create a request template and sign it with SAK. This signed URL can be sent to another process, which can be used to fill in the request details and send the request to the storage service. Authentication is still based on a signature created with SAK. But the signature is sent to the storage service by a third party. Such a proxy mechanism can restrict the valid time, permission sets and the permission for the access to some parts of the storage account.
A shared access signature is also known as a container-level access policy, which replaces the method representing directly in the URL with a certain number of parameters (such as valid time or permission sets). These parameters are actually specified by the access policy stored in the Windows Azure Storage Service. It provides greater flexibility and control over authorization limits, because a container level access policy can be modified or revoked at any time.
In order to support periodic SAK changes without service interruption, a storage account can have two keys associated with itself at the same time (each key has full access to the data). The order of changing the keys is to add a new key to the storage service firstly, and then change the key used in all applications accessing this service. Finally, remove the old key. Changing the authorized storage keys is done through SMAPI or Windows Azure Portal.
Isolation
In addition to data access identity authentication, simply isolating different data appropriately is also a widely recognized way of protection. Windows Azure provides different levels of isolation, Just as the discussion below:
Isolation of Hypervisor, Root OS and Guest VMs
A key boundary is the isolation between the Root virtual machine and the guest virtual machine, and the isolation between the guest virtual machine and another guest virtual machine, which is managed by the Hypervisor and Root OS. Hypervisor / root OS takes advantage of Microsoft’s decades of operating system security experience and the latest Microsoft Hyper-V experience to provide a robust guest VMs isolation.
Isolation of Fabric Controllers
As the core part of Windows Azure Fabric, many important controllers are applied to reduce the possible harm to the Fabric Controller, especially to prevent the potential threat from the Fas which is broken in the user program. Communication from FC to FA is unidirectional – FA implements a service protected by SSL, which is accessed by FC and only responds to requests. It cannot initiate connections with FC or other highly privileged internal nodes
FC strictly analyzes all the returned messages according to the standard of returning the messages back to the untrustworthy nodes.
In addition, FCS and devices that cannot implement SSL are on independent VLANs, which limits the possibility of their authentication interface being exposed to the host node of the compromised virtual machine.
Microsoft’s SDL Policy is also widely recommended to Windows Azure users, because the security of applications hosted on Windows Azure largely depends on the user’s development process. As a guide to this document, the best security practices for developing Windows Azure applications can also be found in Microsoft.com (refer to the reference materials for further reading).
Even if Microsoft and their users follow SDL, there is still a very small possibility of being attacked in the process of developing and deploying to Windows Azure. Just as mentioned above, the users provide their own applications through SMAPI, which uses certificate identity authentication and channels protected by HTTPS, as well as other controllers to transmit codes.
With the spread of global standards including ISO 27001, Safe Harbor and other standards, the importance of business and management specifications is growing rapidly. In many cases, non-compliance with these standards will have a significant impact on the organizations, including catastrophic economic penalties and reputation damage. Any threat discussed above will have an impact on the specification, but there are other threats that are directly related to the failure in operations according to the widely-accepted practices. The ways to verify whether the calibration meets the requirements of laws, regulations and contracts are providing the normal forms of expression to independent auditors, supporting electronic search, and promoting users’ reasonable efforts in other aspects. Microsoft provides users with the information they need to decide whether it is possible to comply with the laws and regulations they need to comply with under Windows Azure, and provides tools to demonstrate the specification when possible. There are some discussions of the methods to help users in Windows Azure below.
Users’ Alternative Geographic Location
One of the important internal challenges of Windows Azure is to balance the compliance requirements, which is also one of the important economic drivers in Cloud Services: a multi system management of the segmented users’ data processed across systems, geography and administration. Windows Azure uses a very simple way to deal with this challenge which is to let the users choose where their data is stored. The data in Windows Azure is stored in Microsoft’s data centers all over the world, and the attribute specific based on the user’s geographical location decide the entry of Windows Azure. Through the user’s initiative choice of geographical location of data storage provides a convenient way to minimize the risk of compliance with the specification.
Visit this site extratorrent to get more info.
For best isaimini please visit this site.
Compliance Control
At different controller levels, this document illustrates the recognized qualified practices of Windows Azure from multiple dimensions. Here are some key security features that conform to the rules:
Table 2: Features Conforming to the Rules
ISO 27001 Certificate
Trustworthy third party certificates have provided a mechanism to protect user data without providing too much access authority to a group of independent auditors who may compromise the integrity of the entire platform. Windows Azure operates on the infrastructure of Microsoft Global Foundation Services (GFS), some of which are certified by ISO27001. ISO27001 is one of the most important international-recognized information security management standards in the world. Windows Azure is in the process of getting more industry certification assessments. In addition to the international certification standard ISO27001, Microsoft is the signer of Safe Harbor and promises to fulfill all its obligations under the framework of Safe Harbor. Although the responsibility for complying with laws, regulations and industry requirements lies with Windows Azure’s users, Microsoft still guarantees to help users with the features that conform to the rules.